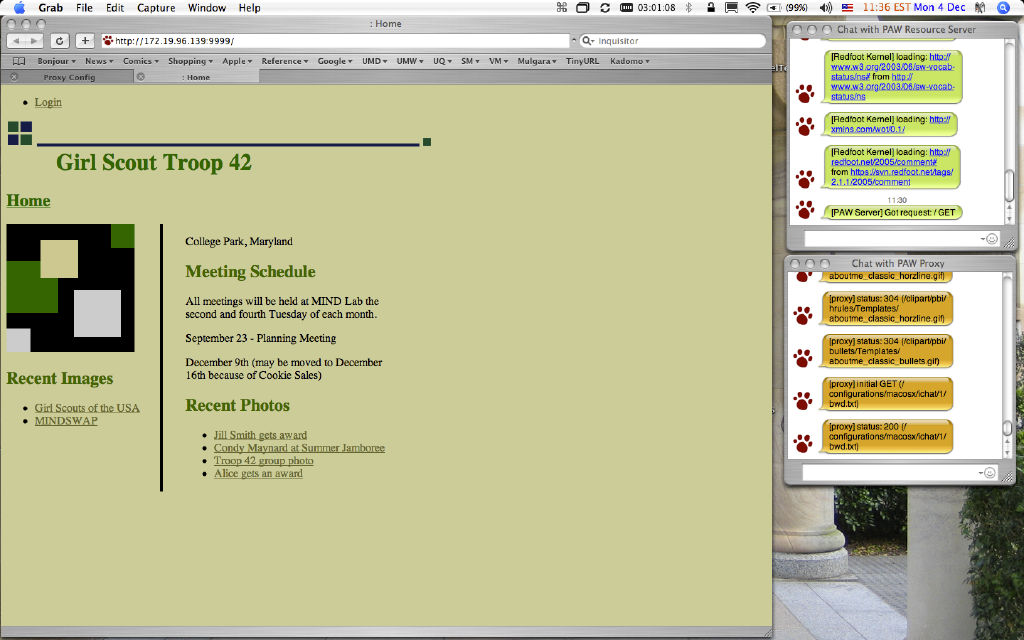
Figure 1. The Home Page for a Fictitious Girl Scout Troop.
We choose to implement a series of three use cases in order to guide our explorations toward real-world goals. The use cases all dealt with the theme of photo sharing on the Web.
Consider a Girl Scout troop. The troop conducts various activities to assist in the social and educational development of girls. Naturally, many people loosely associated with the troop will desire to record some of these activities with photographs. Some will want to share photographs with others via the Web. Under what conditions should photographs of troop activities be released to the general public? To parents of the girls? To relatives of the girls? To friends or acquaintances of the girls? It would be difficult, if not impossible, to determine in advance an access control policy that would make all parents, much less all girls, happy. Different parents will surely want to make different sharing decisions based on the content of the photos, the girls' individual ages and personalities, others included in the photos, etc. In brief, a flexible and distributed policy-aware access control mechanism is needed.
Figure 1 shows the home page of a fictitious girl scout troop. If we are not using a policy-aware Web client, we are unable to see certain content from that site.
Instant message windows are shown to the right of the screenshot. They shown log information from the policy-aware Web server and proxy. The use of the proxy is described below.

Figure 1. The Home Page for a Fictitious Girl Scout Troop.
If we attempt to follow the hyperlink entitled "Condy Maynard at Summer Jamboree", we will get the error shown in Figure 2. That is a standard HTTP 401 (Unauthorized) error, except an additional header has been inserted that provides a URI to the controlling policy.
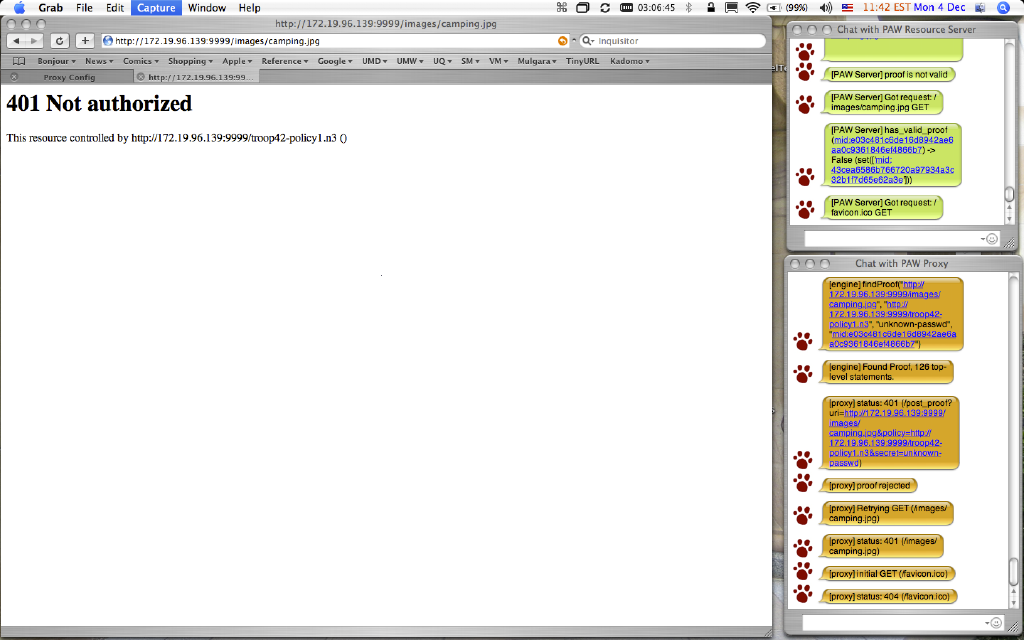
Figure 2. An HTTP 401 Error Message Providing a Pointer to a Controlling Policy.
We can use a policy-aware proxy to emulate policy-aware features in a standard Web browser. Setting our Web browser to use that proxy server and then opening the proxy's Web page shows the situation in Figure 3.
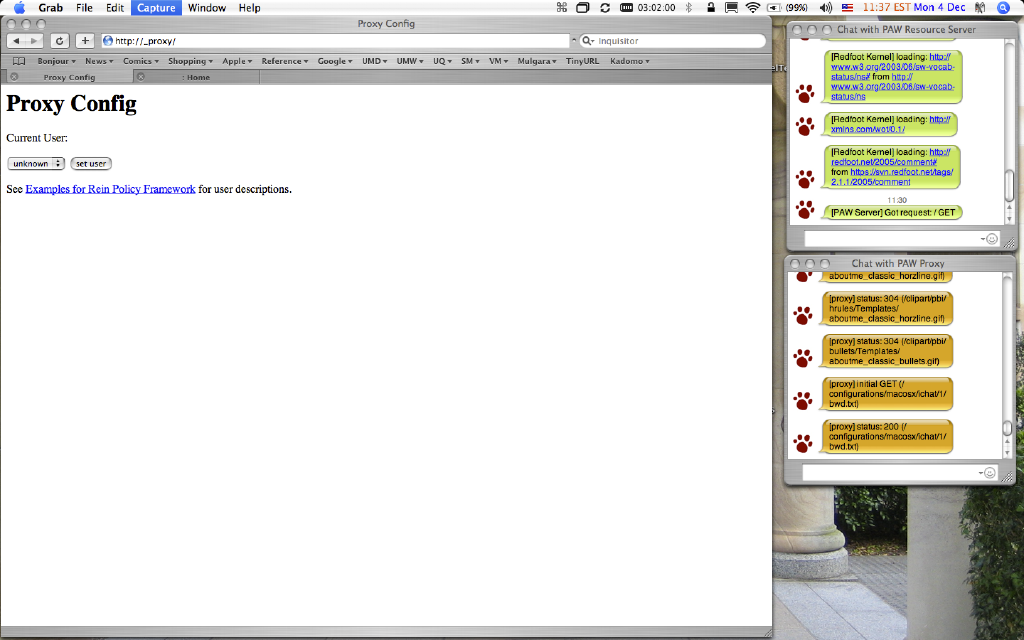
Figure 3. A Policy-Aware Proxy Set with No User.
We can set the proxy to act as a girl scout named Alice. Alice is a member of the troop and attended the jamboree where Condy Maynard's photo was taken. Alice should therefore be able to see the photo. Setting the proxy to act as Alice is shown in Figure 4.
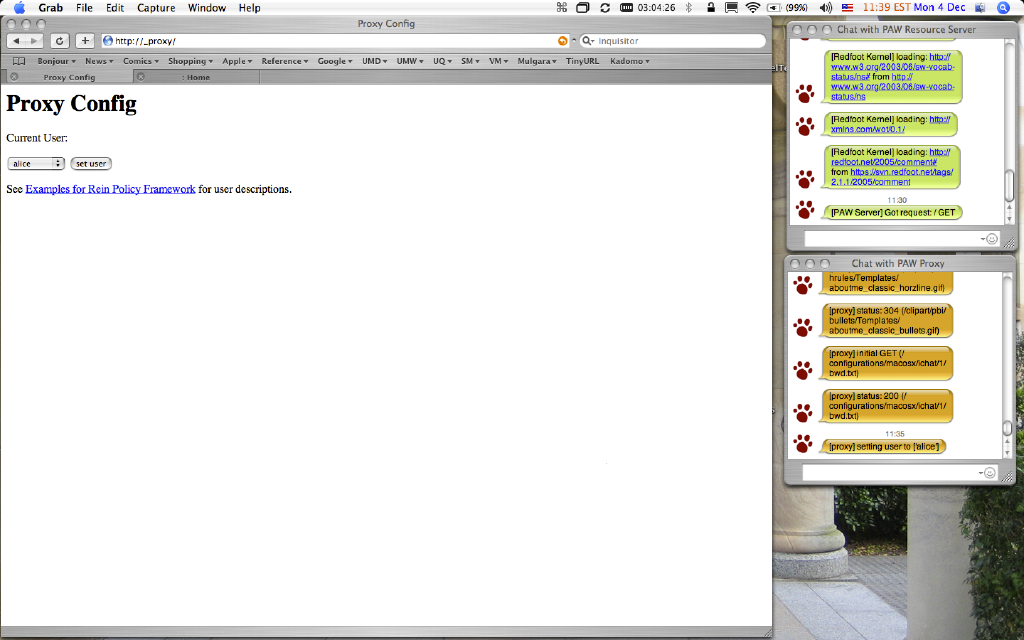
Figure 4. Setting the Proxy to Act as User Alice, a Girl Scout.
With the proxy set to construct a proof as if we were user Alice, we may now follow the hyperlink to Condy's photo. This is shown in Figure 5. Note the log messages from the Web server saying that the proof was valid and from the proxy saying that the server accepted the proof.
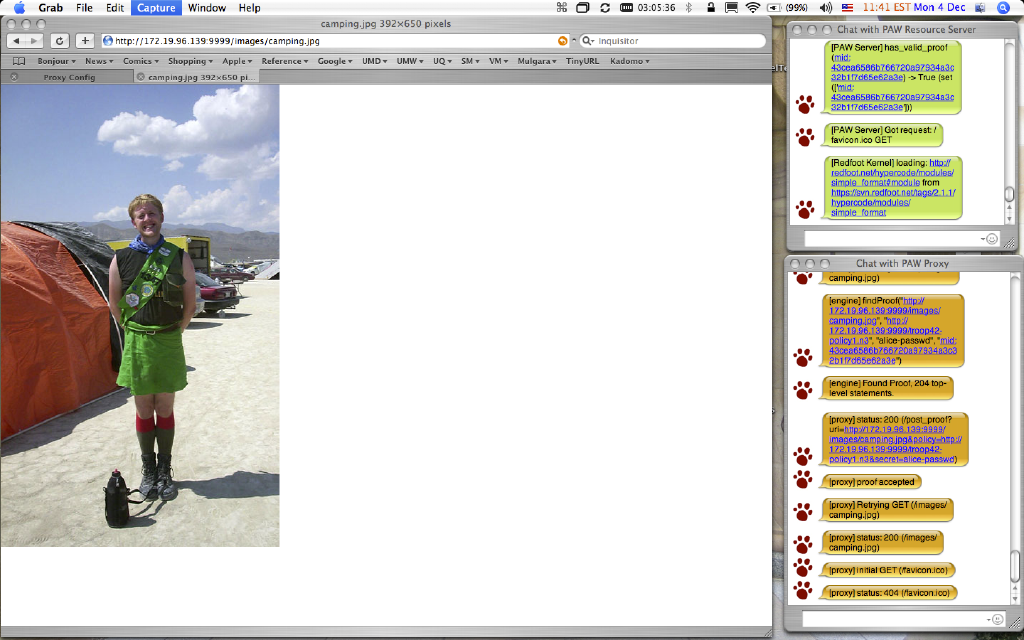
Figure 5. A Photo of A Girl Scout.